Introduction
SCTP is a reliable transport protocol operating over IP. SCTP is more akin to TCP than UDP, however it yields additional features to TCP while still supporting much of the same functionality. So SCTP is connection oriented and implements the same congestion/flow control. Detection of data corruption, loss of data and duplication of data is achieved by using checksums and sequence numbers. A selective retransmission mechanism is applied to correct loss or corruption of data. [1]
In the TCP/IP network model, SCTP resides in the transport layer, alongside TCP and UDP. The transport layer handles communication among programs in a network. This involves accepting data from the application layer, and repackaging it (perhaps fragmenting the data) so it may be passed on to the network layer. In addition the transport layer will also ensure the data arrives correctly on the other end. A transport protocol in essence is a set of rules that govern how data is sent between communicating nodes.
The network layer is used for; basic communication,
addressing and routing, IP is usually used. The application layer consists of
end-user applications and the link layer defines network hardware and device
drivers.
Diagram 1 – 4-Layer Network Model

Comparing SCTP to TCP
SCTP and TCP have some distinct differences, yet also many similarities. In this section we will explore their similarities and then discuss the major ways in which they differ.
Similarities
Startup: to establish an association between two nodes, both protocols
will exchange a series of messages. There are differences in the way these
messages are exchanged and their format, but they hold the same purpose- to set
up an end-to-end connection (association or connection).
Reliability and Ordering: both SCTP and TCP implement mechanisms to
endure the successful delivery of user datagrams. This includes reliable and
ordered data delivery.
Congestion Control: this is a critical element in any transport
protocol. It regulates the flow of data entering the network, limiting it to
accommodate for occurrences of congestion. SCTP and TCP hold the same congestion
control mechanism- Additive Increase, Multiplicative Decrease (AIMD) congestion
window management.
Closing Down: both protocols have two different close procedures, a
graceful close and an abortive one. The graceful close will ensure that all user
data in the queue will be delivered before the association is terminated. The
abortive close occurs during errors.
Differences
There are two key differences between TCP and SCTP:
·
Multihoming
·
Multistreaming
These are new features in SCTP and are what really set the two protocols
apart.
Multihoming: an essential property of SCTP is its support of
multi-homed nodes, i.e. nodes which can be reached under several IP addresses.
If we allow SCTP nodes to support more than one IP address, during network
failure data can be rerouted to alternative destination IP addresses. This makes
the nodes more tolerant against physical network failures and other problems of
that kind.
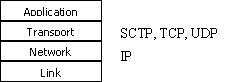
Multistreaming: is an effective way to limit Head-of-Line Blocking.
The benefit in having multiple independent data streams is if a packet is lost
in one stream, while that stream blocks to wait for the retransmission the
remaining unaffected streams can continue to send data. In TCP if a packet is
lost, the connection effectively grinds to a halt while it waits for the
retransmission to be sent [2]. This phenomenon where packets are blocked by a packet
in front which has been lost is known as Head-of-Line Blocking and can be
illustrated thus:
Diagram 2 – SCTP Multistreaming
SCTP
Association
TCP Connection
An SCTP association is equivalent to a TCP connection, they both represent an
end-to-end relationship between two transmitting nodes.
Multistreaming can be achieved in TCP, however it involves opening multiple
TCP connections which each act as a stream to send data. This differs from
multistreaming in SCTP where all the streams reside in a single association.
Opening multiple TCP connections is TCP-unfriendly, which means that a pair of
communicating nodes will obtain a larger proportion of the available channel
bandwidth. Thus, SCTP is more TCP-friendly in this regard.
Although multihoming and multistreaming may be where SCTP and TCP differ
most, the two protocols exhibit other differences, which are also
important to discuss.
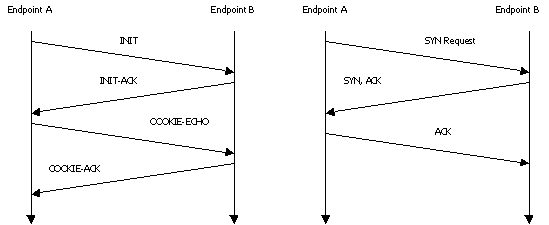
Security at Startup: SCTP and TCP both carry out an exchange of
messages to establish an end-to-end relationship. The way these messages are
sent however, are different. Traditional TCP uses a three-way handshake, whereas
SCTP uses a four-way handshake. A signed state cookie is involved in the SCTP
four-way handshake, which helps to protect from denial of service attacks.
Diagram 3 illustrates the start-up procedures in TCP and SCTP [2].
Diagram 3 – SCTP and TCP start-up
SCTP TCP
A denial of service attack is where resources are
tied up on the server side so that it is impossible to respond to legitimate
connections. The attacker issues vast amounts of SYN requests (a message
requesting set-up of a connection) to the server and when it receives the SYN,
ACK (see diagram 3) it simply discards it, not bothering to respond with an ACK.
This causes the server to retain the partial state that was allocated after the
SYN request, and if carried out repetitively will lead to a denial of service.
SCTP protects against denial of service attacks
with the use of a cookie. The cookie is bundled with the INIT-ACK from the
server to the client. The server does not record the association or keep a
transmission control block (TCB), rather it derives the TCB from the cookie,
which is sent back from the client inside the COOKIE-ECHO. Since it has no
knowledge of the association till the client responds with a COOKIE-ECHO, it
becomes resilient to denial of service attacks.
There may at first appear to be an overhead to
sending four messages, however user data can be bundled in the last two SCTP
packets.
Data Delivery: Data transmission
in TCP is byte-stream oriented; in SCTP, it is message-oriented. In TCP, data is
transported as a consecutive stream of bytes between two endpoints, so user
message boundaries are not preserved when they are on the wire between two end
points. Parts of one message may be sent with parts of another message, in a
single data packet. This means that some kind of message-delineation is required
by the application, to inform the receiver, the message length and the amount to
read. The receiving application will need to do some complex buffering and
framing to reconstruct the messages.
SCTP, in contrast, makes an explicit demarcation
of user message boundaries. Each message is delivered as a complete read, which
lifts a lot of the work off the application layer. An exception to this is when
the message is larger than the maximum packet size. Although, parts of two user
messages will never be put into a single data packet.
Unordered Delivery: SCTP allows for data to
be sent reliably but unordered. This has benefits when dealing with large
amounts of independent transactions, e.g. components in a web page.
TCP has no such facility.
SACKs: All acknowledgements in SCTP are
with SACKs. They are useful as they indicate if there are any gaps in the
transmission, i.e. missing blocks. TCP does not make explicit use of SACKs but can be configured to support them. However, TCP can only report four missing
data packets in a SACK, SCTP allows for much larger amounts to be reported.
Closing Association: Despite the fact that
both TCP and SCTP have graceful close mechanisms, there is a slight difference
in what these mechanisms permit. TCP allows what is known as the
“half-closed” state, where one endpoint stays open while the other endpoint
closes. SCTP does not allow this, both endpoints must close when the shutdown
primitive is issued. One reason for not putting the half-closed state in SCTP
was the lack of use of it: very few applications require it.
Transport Protocol Functional Overview [2]
|
Protocol Feature |
SCTP |
TCP |
UDP |
|
State required at each endpoint |
Yes |
Yes |
No |
|
Reliable data transfer |
Yes |
Yes |
No |
|
Congest control and avoidance |
Yes |
Yes |
No |
|
Message boundary conservation |
Yes |
No |
Yes |
|
Path MTU discovery and message fragmentation |
Yes |
Yes |
No |
|
Message bundling |
Yes |
Yes |
No |
|
Multi-homed hosts support |
Yes |
No |
No |
|
Multi-stream support |
Yes |
No |
No |
|
Unordered data delivery |
Yes |
No |
Yes |
|
Security cookie against SYN flood attack |
Yes |
No |
No |
|
Built-in heartbeat (reachability check) |
Yes |
No |
No |
References
[1] R. Stewart et al., RFC 2960: Stream Control Transmission Protocol, IETF, October 2000.
[2] R. Stewart and Q. Xie, Stream Control Transmission Protocol (SCTP): A Reference Guide, Addison Wesley, 2002.
[3] SCTP for Beginners: http://tdrwww.exp-math.uni-essen.de/inhalt/forschung/sctp_fb/
[4] SCTP overview: http://www.sctp.org/sctpoverview.html
![]()